Review some basic concepts in the information technology majors - Part 3: Basic information about security
Bài đăng này đã không được cập nhật trong 4 năm
A. Basic Security information
I. Define of Security Information
In my opinion, security is a stable or stable state by a company, a state, or a nation, so that everyone in society follows a common standard. Thus, the company, the country can hold or develop. And infringements, security breaches will certainly be punished and the level of punishment will be based on the degree of danger of the infringement. In all, infringing on national security is the heaviest crime, which can be punishable at the highest criminal level.
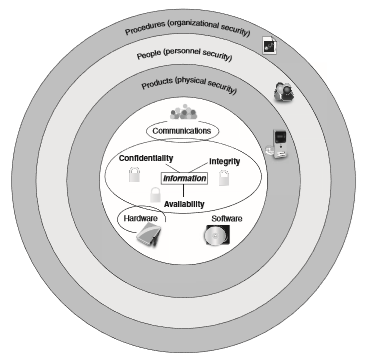
Because of the development of technology, and the social stage 5.0 is about to be universal. People are not going to carry their computers or things to work anymore, everything just comes from the little phone in your hand. "Automation" has been around the globe. And the user information, customer information, etc. have become increasingly valuable. And in order to protect and respond to their customers' safety and information, the term "information security" is born. Information security is both a means of protecting information and the process of protecting it. In the IT world, information is considered perfect when it meets three characteristics CIA:
- Confidentiality
- Availability
- Integrity
In addition, there is another standard for information protection, which is AAA:
- Authentication: Authentication is also known as identity authentication. When you access an account in general and a customer information language, you must declare that you are not an impostor. Not only that, because the rights of each person in the machine were admin to meet with each position, with each account. Therefore, only admins or authorized persons can access such information.
- Authorization: For each information, or account of each person in the company are administrators for their own rights and different. For example, employees only see some information (such as customer name, age, address, contact phone number, etc.), the accounting department retrieves the customer card information and invoices. In short, you can do these jobs unless you are granted the right.
- Accounting: all actions such as login, purchase, ... from the web address, at some point, ... are stored on the hard drive of the computer in the server. In order to ensure the confidentiality of information, the data must be safeguarded.
A comprehensive definition of information security involves both goals and processes. Information security may be defined as that which protects integrity, confidentiality, and availability of information on devices that store, manipulate, and transmit information through products, people, and procedures.
II. The importance of information
In the 1980s we witnessed the enormous growth of information technology and its importance in social organizations as well as in the economics of new data. Most of the US computer magazines tell us that every day the US business community produces nearly 700 million pages of informatics data, 235 million photocopies, and nearly 78 million letters. They also say that the amount of information this year will increase by about 25%.
It was only the first information, in the 1980s, of the previous generation. With the development of technology, life 5.0 is about to adopt globalization, more and more information is born. computers, telephones, ... and other electronic devices are produced non-stop. Up to now, the average person now has to own about two electronic devices, which can be phones, laptops, smartwatches, etc. For example, a company now plans to develop a company, make a project, or make a client list that is familiar and supportive of the company. If that information is stolen or stolen, that company will be on the brink of bankruptcy is normal. In addition, those customers do not want to be publicly disclosed for a variety of reasons. At the same time, the attacker can claim ransom from the company and from the customers listed. That's just an example of the small amount of information, with more and more information at the exponent level, the amount of money to ransom them is also increasing. Therefore, information is extremely important and should be kept absolutely confidential. Only competent persons may use them but shall not be used for the personal interests of such persons but for the common interests of all persons.
III. The following dangers and safeguards are in place to protect the information before and after the threat.
There are 5 steps to secure your data and information:
- Step 1 - Encrypt the data
- Step 2 - Use strong password
- Step 3 - Two-step verification
- Step 4 - Protect your network
- Step 5 - Use antivirus software
Data security threats are both hardware and software of the computer.
1. Hardware
When a network security problem occurs, the hardware of the individual or organization may be damaged, flickering, not working properly.
2. Software
One of the most worries of enterprises, when the incident occurs, is safety information lost, damaged, altered content. More dangerous, hackers can steal all the data and force the victim to pay a ransom.
3. Attacked by malware
Hackers can use various attack techniques to penetrate into the system such as Phishing, viruses, spyware, man in middle.
4. Loss of safety information due to using Email, social networking
Hacker attacks today are very sophisticated and varied. They can use the Phishing technique to send attachments in malicious emails, then ask the user to click on the link/file and follow the instructions. As a result, the victim may be hacked to transfer money or computer victims are exposed to data, infected with malicious code. In addition, the risk of disclosure of information on the social network is very high if the user does not fully secure a personal account on Facebook, Youtube, etc.
5. Loss of safety information for the Website
Some damages caused by the loss of information security to the Website may be hijacked, hacked web site, the suspended website can not access, changed the website interface, dirty link insert, attacked Dos, lost project documentation, lost client list ...
6. Some ways to handle risks
- Avoid risk: Avoid risks associated with risk prediction and decision-making by people who know them.
- Accept risks: Risks are accepted and resolved at the risk. For example, if you lose your car, you accept it and go buy a new one.
- Slightly: Mitigation is a means of addressing risk by providing the least risk and the least possible impact.
- Deterrence: The deterrent of today is dependent on the law. Due to the deterrent of the law, many risks are not only reduced but also disappear.
- Conversion: It is very difficult to define this measure, but by the following example, you can see that it is easier to understand than the definition. If you have an accident, the risk you have is that you have an accident. And many consequences such as hospitalization, drugs, money. And to minimize that risk, you switch to a third party. That is, you use the insurance company's benefits, and they will support you, give you a portion, and thus reduce the risk enough.
All rights reserved